Hello guys,
Today I will show you how to install Backtrack 5 and Metasploitable-Linux on Vmware,
This Tutorial is just to get you guys ready to my Metasploit videos that I will release very soon.
First of all, you should download both Metasploitable-Linux (Our Target) and Backtrack 5 (Our attacker)
Download Backtrack for HERE
Download Metasploitable from HERE
Download VMWARE Player from HERE
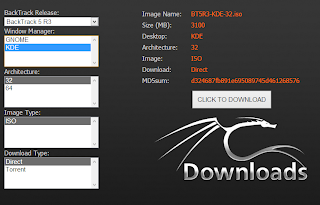
When you download Backtrack, make sure you downloaded for 32-BIT Architecture.
I prefer KDE, which I will be using, and it always works on vmware. (GNOME give some graphics errors sometimes)
Today I will show you how to install Backtrack 5 and Metasploitable-Linux on Vmware,
This Tutorial is just to get you guys ready to my Metasploit videos that I will release very soon.
First of all, you should download both Metasploitable-Linux (Our Target) and Backtrack 5 (Our attacker)
Download Backtrack for HERE
Download Metasploitable from HERE
Download VMWARE Player from HERE
When you download Backtrack, make sure you downloaded for 32-BIT Architecture.
I prefer KDE, which I will be using, and it always works on vmware. (GNOME give some graphics errors sometimes)
Backtrack Installation
After you download backtrack, open vmware, and click on "Create A New Virtual Machine"
Then check "Installer disc image file (.iso), and browse for your backtrack image file, and open it.
Now click on Next, and choose "Linux" as the Guest operating system, and "Ubuntu" as the virsion
Click on "Next", Choose a name for your OS, any name is OK!
Now click on "Next" again, now it's your turn, you choose what disk size you want for it, and then click on Next again, then you're done! UNLESS, you want to edit some of the settings, and CPU & RAM for your OS, you can do by clicking on "Customize Hardware"
Now Play your virtual machine, wait for it until it shows a terminal saying "root@bt:~#"
type "startx" and click enter.
You're done!
Metasploitable-Linux Installation
Metasploitable is a vulnerable OS, it has many vulnerabilities.. We will use that OS as a target to pwn it..
When you download Metasploitable, it will be downloaded as a .zip file, extract it, and you will see a file with the extension .vmx
All you have to do to install this OS, is to double click on it.. vmware will ask you if you you copied the virtual machine, or moved it, click on I moved it!
And you're done!
Hope you liked it! =)